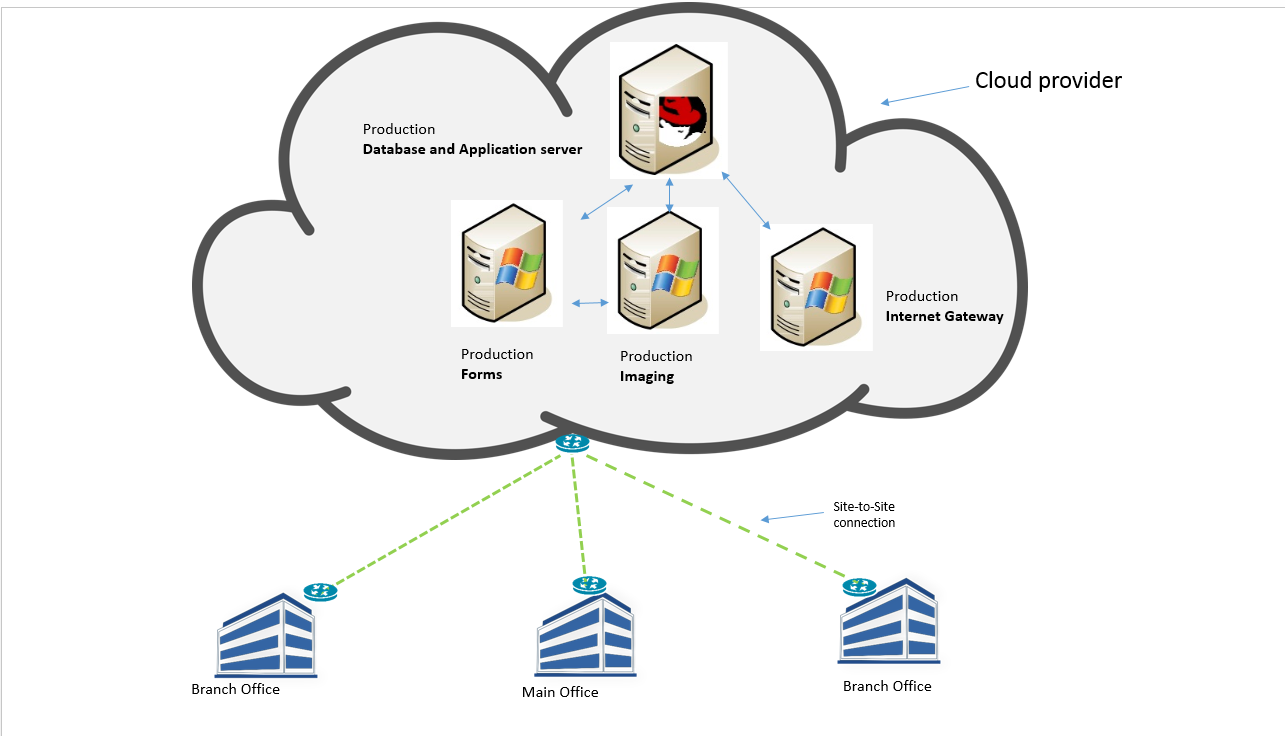
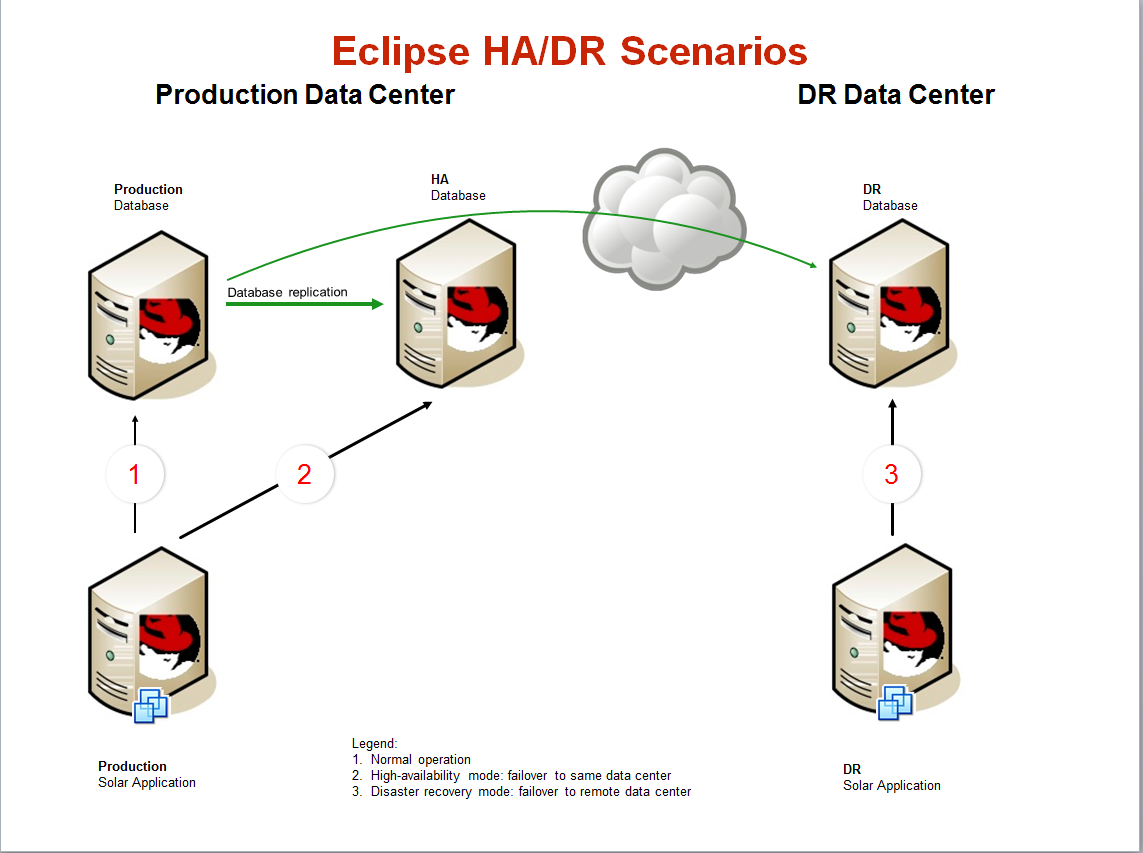
Summary
Epicor Eclipse is aware of the Meltdown-Spector vulnerabilities affecting many modern microprocessors from Intel, AMD, POWER and ARM chips that could allow hackers to access a computer’s memory and steal passwords, encryption keys and other private information from open applications.
Because it’s a vulnerability in the CPU hardware implementations, not a bug in the Eclipse application program, there is no “patch” from Eclipse.
We recommend that customers to check with their hardware and Operating System (OS) vendors for applicable patches as the solution for Meltdown and Spectre.
Epicor’s Response
- Apply the firmware update via BIOS update
- Apply the operating system (RHEL, Windows and AIX) patch
- Apply hypervisor patches where applicable
Recommended Customer Actions
We recommend that customers to open a service request with Eclipse Systems support team and deploy patches on their platform and underlying infrastructure on a mutually agreed schedule.
Frequently Asked Questions
Q: How do I patch my system?
A:Install Red Hat updates.
A:Install Dell Firmware Update.
Q: Will these fixes slow down my server?
A: Yes, there is performance impact caused by additional overhead required for security hardening, but the actual performance degradation that customers see may vary considerably based on the nature of their workload, hardware configuration and system constraints.
Q: Can I disable these fixes?
A: Yes, you can disable the kernel patches if you fell confident that your systems are well protected by other means. Please see this article from Red Hat for a step by step instructions.
References: