The Epicor Automated Backup Solution (ABS) uses CrashPlan PRO to product Eclipse customers with data backup both on-site and at a secure off-site location. The ABS Failover offering utilizes this off-site backup to offer hosting for customers a disaster situation.
The product is currently available for Eclipse Customers running Linux and Windows servers. The ABS software is installed and configured by Epicor.
There are three levels of backup for the ABS product:
- Tier 1 – CrashPlan PRO software alone offers the ability for local backup copies within the customer network
- Tier 2 – ABS Off-Site Backup: adds the protection of a secure, off-site backup
- Tier 3 – ABS Failover: adds the ability to failover to Epicor’s hosting environment
The CrashPlan PRO software used by ABS offers:
- Local or off-site data backup storage in a secure location
- Byte differential backups, using compression and de-duplication for efficient transportation and archiving
- Incremental, backup versions
- Email backup alerts and reports
- Data is encrypted during transport and backend storage
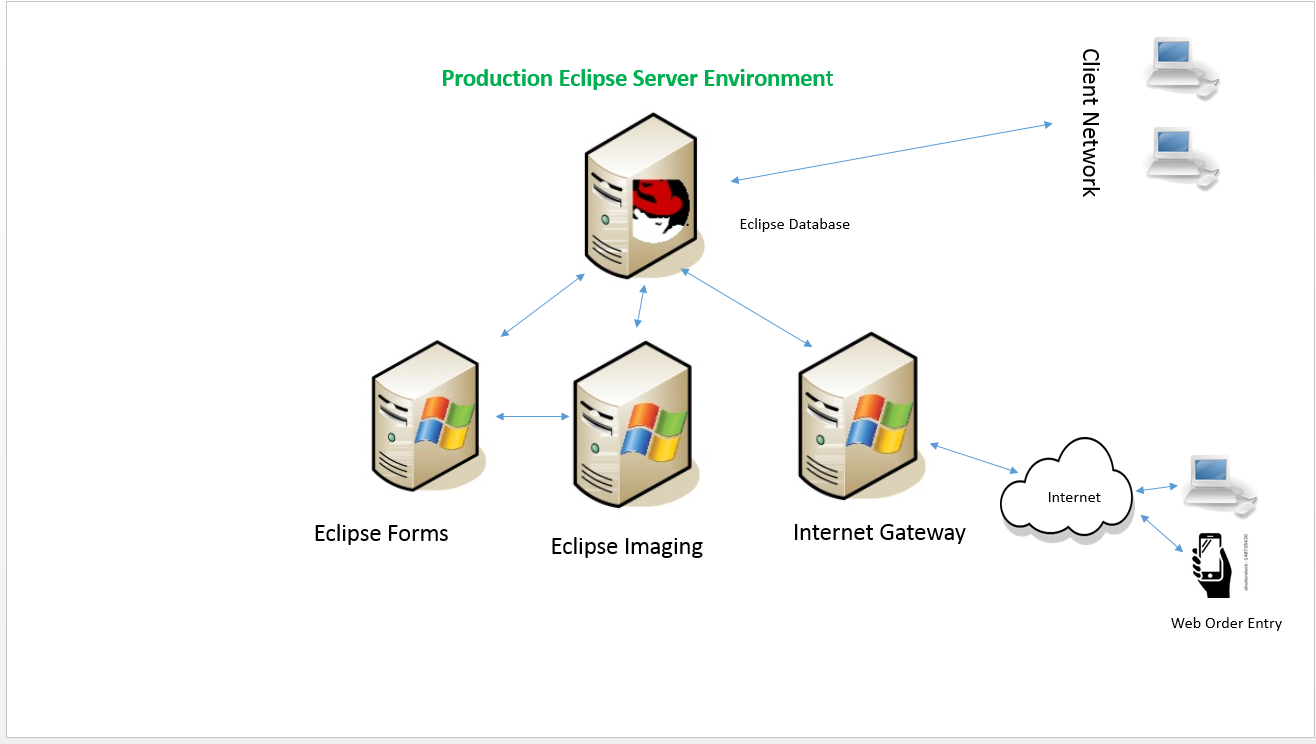
- Failover for Epicor Eclipse systems (Eclipse Database, Forms, Imaging and Internet Gateway servers)
Contact your inside sales representative for more information and pricing.